#Cryptocurrency Cryptocurrency exchange Ouyi has had a series of incidents where user accounts were hacked and assets were stolen. It is not clear whether it is a user problem or a vulnerability in the Ouyi platform. Ouyi has not responded yet. For large investors, if it is not necessary, it is recommended to transfer assets to hardware wallets, which can greatly improve the security of assets. View the full text: https://ourl.co/104383
Earlier, a huge amount of assets of an investor in the cryptocurrency exchange Binance was stolen. At that time, the extension installed by the user was infected and stole the login cookies. However, there was a problem with Binance’s security policy and it did not bind the IP address. If the login was successful and the cookies were bound to the IP address, the hacker would not be able to continue to manipulate the account even if he stole the cookies.
However, the main cause of the theft of investors’ assets in Binance is still the users, because the installation of malicious extensions allowed hackers to steal huge amounts of funds through cross-trading.
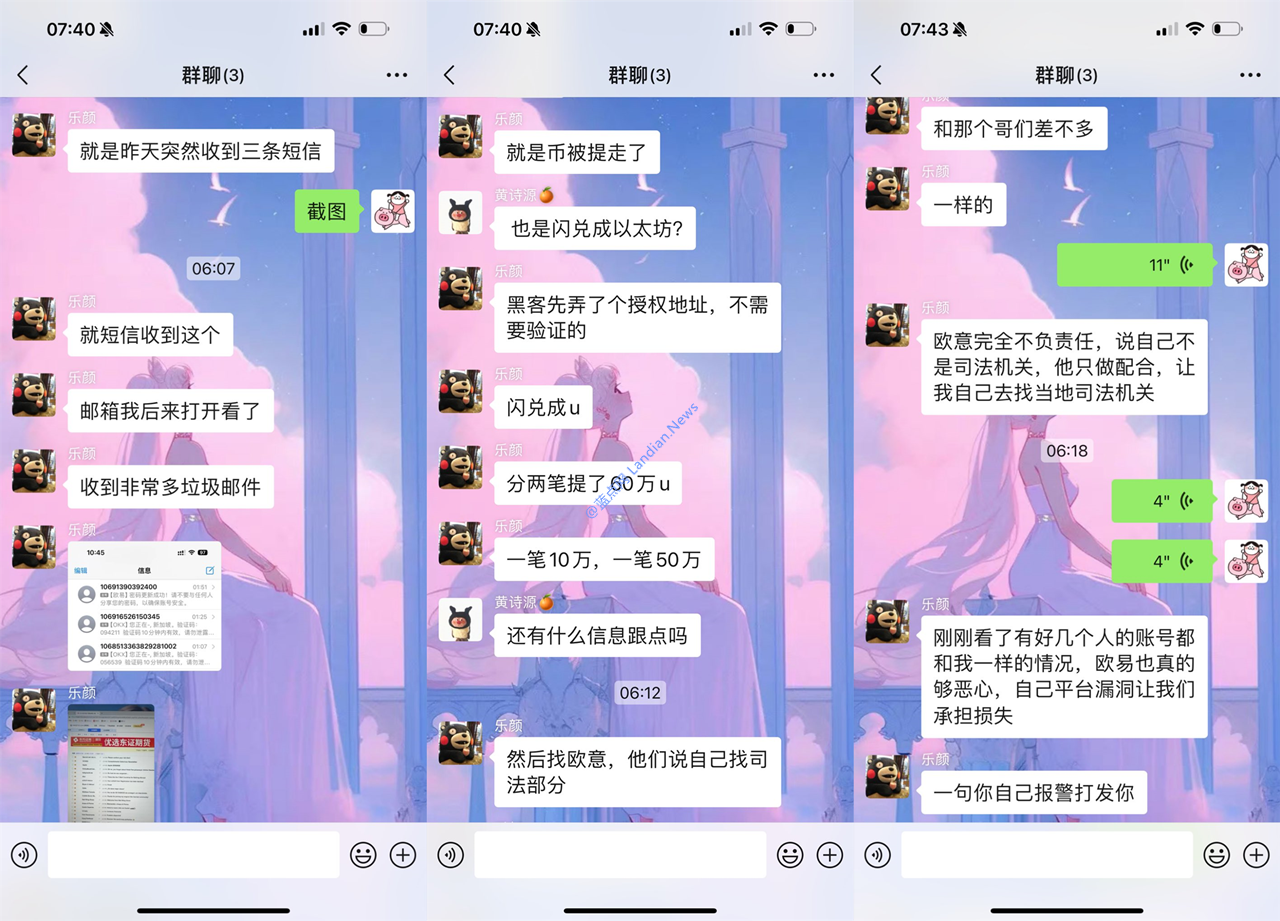
The theft of several user assets at the cryptocurrency exchange OKX this week is a bit confusing. The users did not install malicious extensions and their SIM cards were not hijacked. OKX is currently taking a tough stance, asking users to seek help from law enforcement agencies. The exchange only responds to requests from judicial authorities to cooperate with investigations.
Ouyi has not responded to this matter yet and has not issued any announcement to explain it, so it is not clear whether there is a loophole in the Ouyi platform or it is entirely the user’s responsibility. However, for security reasons, users are advised not to place large amounts of assets on the exchange. If possible, it is best to withdraw them to a hardware wallet.
The currently known information includes:
1. The user has not been attacked by a SIM card swap, i.e. the phone number is still under their control;
2. About 600,000 USDT of known users’ assets were withdrawn, equivalent to about RMB 4.35 million;
3. Before/when the assets are transferred, the user receives a large number of SMS verification codes from OUYI;
4. Before/when the assets are transferred, users receive a large number of email verification codes from OUYI;
5. The hacker’s login IP belongs to Singapore, and the hacker added a withdrawal authorization address through unknown protection;
6. Another known user’s assets of approximately 800,000 USDT were withdrawn, equivalent to approximately RMB 5.8 million, and the withdrawal verification was completed through a mobile phone verification code.
Too much unknown information:
The current logic of withdrawing money from OUYI is that no verification is required for whitelisted addresses. You can withdraw money by clicking it. However, when adding a whitelisted address, you need to verify the email + 2FA verification code or SMS verification code; if you withdraw money from a non-whitelisted address, it is the latter, and two parameters need to be verified.
It is not clear whether the two known stolen users have bound 2FA verification tools such as Google Authenticator. Ouyi itself can skip 2FA and choose to use SMS verification code instead, so there is a security weakness here.
Secondly, some of the stolen users were given API addresses that included transaction and withdrawal permissions. After the API was activated, the hacker could operate it directly, but identity authentication was also required to activate it.
So the current question is, where do hackers get the user’s email verification code and 2FA verification code or SMS verification code? Without the verification code, neither withdrawing money nor opening the API is possible.
As for the user’s own information, such as login email or mobile phone number, such leakage has become commonplace. Obviously, hackers are targeted, that is, they screen users in advance and then carry out targeted attacks to ensure success at one time.
possible reason:
At least for now, we cannot say that there are security loopholes in the Ouyi platform itself and that they have been exploited by hackers. At this stage, the information provided by the stolen users is not sufficient to prove that there are loopholes in the platform, but there is still a pitfall here, which is the sender of the verification code.
Previously, there have been cases where the email and SMS suppliers of exchanges were hacked, resulting in the leakage of user information. In a sense, if hackers invade these suppliers or collude with insiders, they can indeed obtain the verification code. This operation is more difficult but it is also a direction that can be used as a reference.
Therefore, unless Ouyi himself responds, we may never know the truth of these issues. I hope Ouyi will stop behaving like an ostrich. After all, screenshots of these thefts are circulating in the cryptocurrency circle.
There is also a fake face video that deceived Ouyi to get the account:
Earlier, Ouyi had a user asset theft problem. At that time, the hacker seemed to have used AI to forge the user’s video. If Ouyi was bound to 2FA and lost it, it was necessary to contact manual customer service to handle it.
The hacker took advantage of this link and used a fake facial video to trick Ouyi into resetting his 2FA information. Since 2FA was controlled by the hacker, the account assets were naturally not immune. In this case, Ouyi should bear full responsibility.
Limited time event recommendations:Alibaba Cloud Server 36 yuan/year rush purchase、Tencent Cloud 30M bandwidth Singapore server、QQ Super Club 15 months 108 yuan、B station membership 88 yuan。